Image documents use multiple file formats. The most common are: TIFF, JPEG, PSD and RAW. Each of these formats has its own rules on how to store the associated metadata.
There are also multiple standards and formats for metadata that allow informative data to be included in digital images. Each specifies how metadata should be stored, ordered and encoded, as well as the semantic grouping that defines the metadata representation (e.g. character strings, numbers, arrays, etc.).
Some metadata is read-only, while other metadata can be modified by the user. Some metadata is implemented by a single standard, while other metadata (e.g. copyright) is implemented by several standards, using similar semantics, but with subtle differences.
1. Types of Metadata
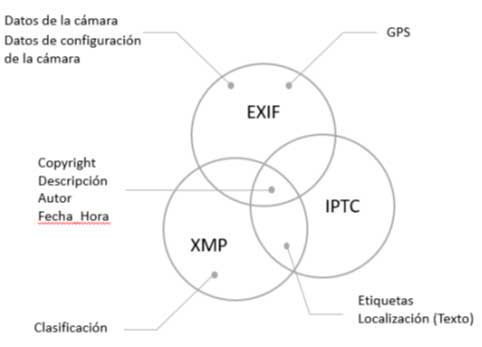
The main standards that exist for the definition of metadata in digital images are: EXIF, IPTC and XPM.
- EXIF - Exchangeable Image File Format.
EXIF is the metadata format most commonly used by digital cameras. It defines a set of tags (tags), which describe the characteristics of the camera (manufacturer, model, software, etc.), and its configuration at the time of image capture. The EXIF metadata also contain the location coordinates in case the camera is GPS-enabled, as well as other descriptive metadata such as title, author, copyright etc.
- IPTC - International Press Telecommunication Council.
IPTC is a consortium of leading news agencies and media companies. In IPTC, news industry organisations develop and maintain technical standards to improve and standardise the exchange of news among the world's news agencies.
- XMP - Extensible Metadata Platform.
XMP is a standard that defines a model for metadata creation and processing, based on XML tags. This model uses one metadata schema to store basic properties, and another for each device or application to store its own information. In this way, each application can use this common method to capture and share its metadata.
Some types of metadata are created and used exclusively by one of the standards. Other types of metadata are implemented by more than one standard.
The following figure and table show metadata shared across the three standards and metadata used exclusively by one of them.
The latest versions of XPM already allow mapping of almost all EXIF and IPTC metadata.
2. Metadata and Cybersecurity
The first objective of an attacker is to gain access to the victim's systems, for which the extraction and analysis of this metadata is one of the preliminary tasks of any attacker who wants to gain access to the systems. This facilitates, among other things, the task of discovering passwords (using methods such as dictionary attacks, brute force attacks, etc.), or to carry out social engineering attacks, or even, based on the software versions detected, to know which Exploit to use to exploit vulnerabilities.
For this reason, great caution should be taken when publishing images with metadata on the corporate website, which individually do not seem to represent a great risk, but which, if analysed together, can represent a serious vulnerability for the organisation's systems.
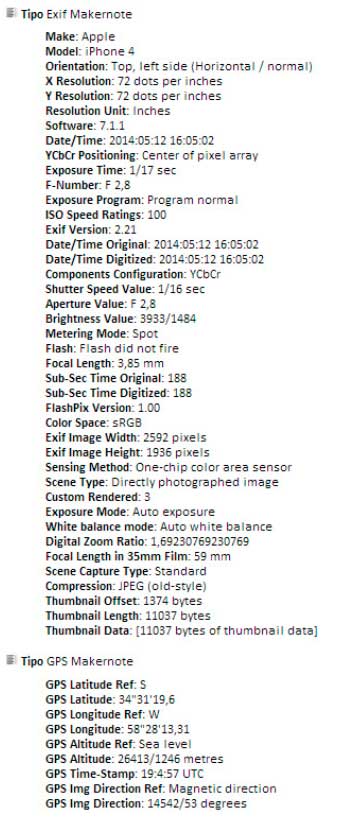
The following shows the metadata of a simple photograph, and how it can be used to obtain very useful information for a cyberattack.
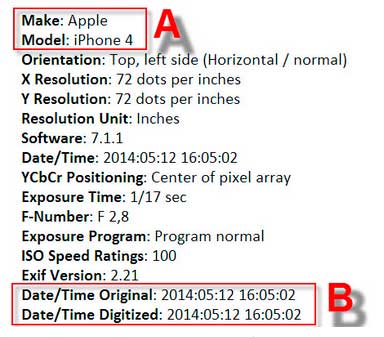
Among many other details, you can see, firstly, the make and model of the device with which the photograph was taken, and secondly, the exact date and time.
The following screenshot shows this in detail:
This kind of information might seem simple and insensitive, but it could simplify things for an attacker, as knowing the type of device his potential victim uses, he will be able to look for the right exploits, for example. In the screenshot above you can also see the operating system version, which will lead you to know which vulnerabilities could affect the computer.
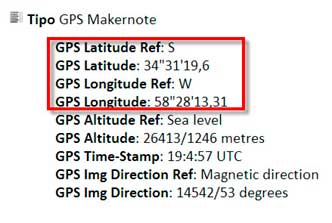
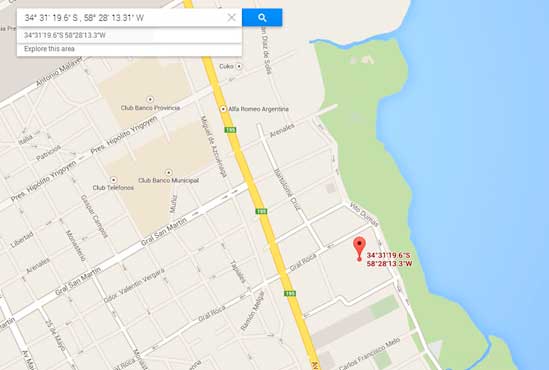
However, the most sensitive information in this case is the geographic location, which reveals the exact location of the user:
Given the widespread mobile connectivity available today, it is not uncommon for people to take pictures of themselves on holiday and upload them to social media. With this GPS information, a cybercriminal could know that the person who took the photo is away from home.
Taking advantage of free services available on the Internet, such as Google Maps, coordinates can be placed to find the location on a map, as shown below:
We can conclude then that files uploaded to the cloud can tell more than meets the eye. This type of information leakage can be avoided by using any of the applications that MetaClean makes available to you.
MetaClean Control is a powerful tool for searching, deleting and editing the metadata of Microsoft Office (Word, Excel, PowerPoint and Visio), Open/Libre Office (Text Documents, Spreadsheets and Presentations), PDF and Image, Audio and Video files (more than 100 different file types).
MetaClean is an application that can be easily installed in Server architecture as well as in PC or Laptop, its operation is very simple and intuitive and does not require an internet connection for its operation, making it ideal for isolated environments.
REFERENCES